Hack The Box (HTB) challenges are an excellent way to hone your cybersecurity skills, and the Aliens HTB Write Up is no exception. This guide unpacks every step required to solve the challenge while providing a detailed walkthrough, offering insightful solutions, and enhancing your understanding of penetration testing.
Understanding the Aliens HTB Challenge
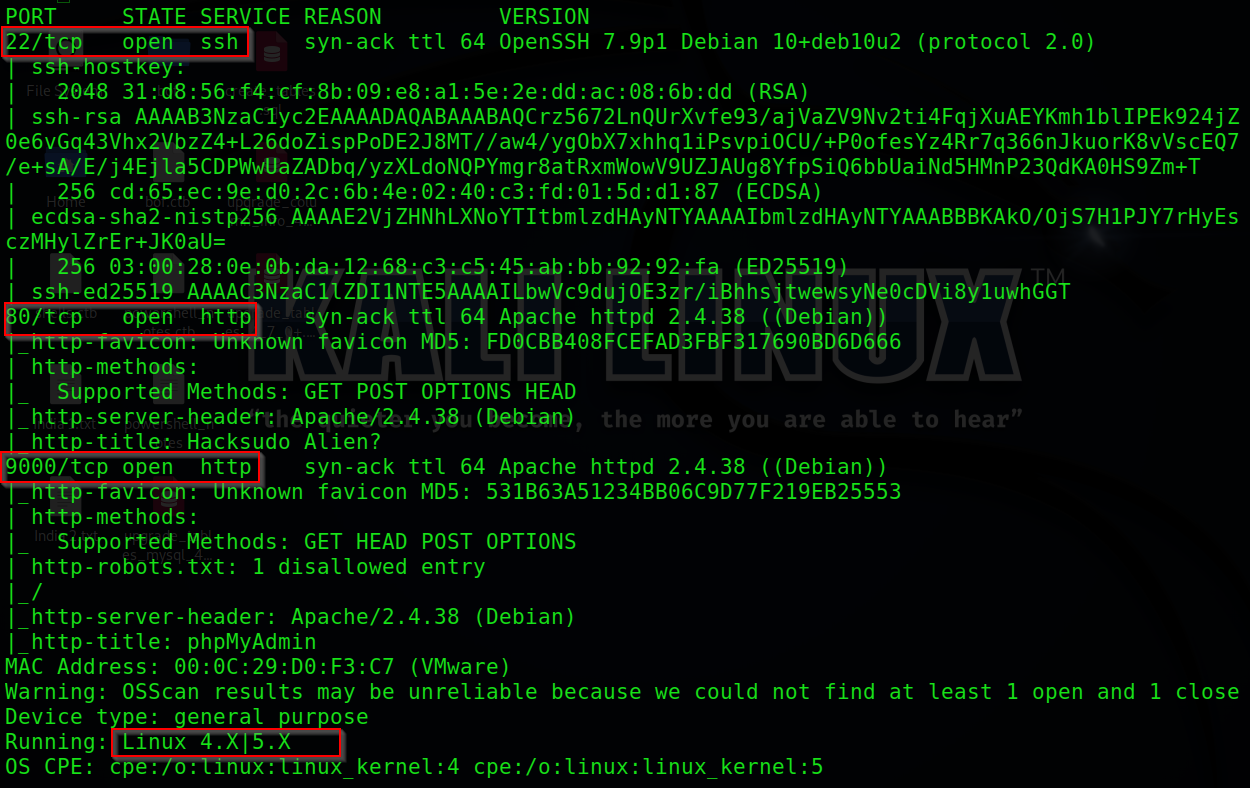
The Aliens challenge on Hack The Box (HTB) is a CTF (Capture the Flag) task that demands technical knowledge and strategic thinking. The goal is to infiltrate a virtual machine, uncover vulnerabilities, and retrieve flags. It tests multiple skills, including enumeration, exploitation, and privilege escalation.
Why is the Aliens HTB Challenge Unique?
- Features a complex yet fun sci-fi theme
- Requires multi-step exploitation
- Offers valuable lessons for penetration testers
During the enumeration, you may discover an HTTP service running a web application. Further exploration often reveals a potential attack vector.
Steps to Exploit Initial Vulnerability
- Examine source code for clues.
- Use Burp Suite to intercept and modify requests.
- Leverage vulnerabilities, such as SQL Injection or file inclusion exploits, to gain access.
Privilege Escalation
After gaining a foothold, the next step involves escalating privileges to root. This process may involve exploiting kernel vulnerabilities, misconfigured permissions, or scheduled tasks.
Capturing the Flags
Types of Flags
- User Flag: Found after gaining initial access.
- Root Flag: Obtained after privilege escalation.
Troubleshooting Common Issues
Issues and Solutions
- Firewall blocking access: Use proxy tools or VPN.
- Permission denied errors: Check file ownership and permissions.
- Failed exploits: Research alternative methods and verify prerequisites.
Key Takeaways from Aliens HTB Write Up
Lessons Learned
- Always enumerate thoroughly.
- Understand the underlying vulnerabilities before exploiting.
- Document every step for future reference.
Additional Resources for HTB Challenges
- Hack The Box Forums: A community of enthusiasts sharing tips.
- CTF Write-ups: Online blogs and GitHub repositories.
- Cybersecurity Tools: Tools like Metasploit, John the Ripper, and Nikto.
Also read: Busbis 1660 Disruptive Technologies: Shaping the Future
Conclusion
The Aliens HTB Write Up exemplifies the thrilling challenges Hack The Box offers to cybersecurity enthusiasts and professionals alike. Through careful enumeration, strategic exploitation, and methodical privilege escalation, this challenge provides an excellent opportunity to sharpen your penetration testing skills. It underscores the importance of persistence, problem-solving, and learning from failures.
FAQs
How do I prepare for the Aliens HTB challenge?
Start by brushing up on enumeration tools, web exploitation techniques, and privilege escalation practices.
What tools are essential for solving HTB challenges?
Tools like Nmap, Burp Suite, Gobuster, Metasploit, and Hydra are invaluable.
Can beginners solve the Aliens HTB challenge?
Yes, with persistence and the right resources, beginners can complete this challenge while learning extensively.
What is the role of scripting in HTB challenges?
Scripting automates repetitive tasks like directory enumeration, payload generation, and post-exploitation activities.
Why is privilege escalation necessary?
Privilege escalation ensures complete control over the system, granting access to the root flag.
Are HTB challenges realistic?
HTB challenges often simulate real-world scenarios, making them an excellent learning tool for cybersecurity professionals.